For the last year or so, erroneous reports of “hacked” baby monitor systems that are WiFi enabled have been perpetuated by the media–and trickled down to our readers, who understandably email us to ask about the potential of danger with WiFi baby monitors like the D-Link Baby Camera (above) or the Angelcare AC1200 baby monitor. Of course we wouldn’t recommend them if we thought they were wildly unsafe–though whether you need a video monitor or not is entirely up to you. Also, we don’t blame parents at all for being freaked out of the idea of a stranger virtually in your home–let alone one talking to your baby or toddler somehow.
That said, the chances of that happening are beyond small. Not that it can’t happen, but it’s unlikely.
UPDATE: Please see our post on Fighting hackers: Expert tips for protecting your webcams, baby monitors, and connected devices
The so-called “hackers” in these particular news stories have not been predators or burglars; they turned out to be people (okay, jerks) who stumbled onto an unsecure WiFi network and took advantage. That’s not actually hacking, although it sure sounds better in news headlines. In other words, any stranger trying to use your WiFi network is most likely looking for a free connection, so…don’t give him one.
Here’s how to put your mind at ease if you’re using a monitor with a wireless connection that transmits the signal your laptop or mobile device.
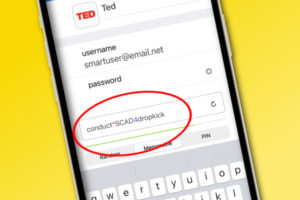
1. Password protect your WiFi connection, also known as your router.
2. Use strong passwords. As you may know by now, the strongest passwords are a combination of numbers, upper and lower-case letters, and characters if allowed. In a nutshell, make combinations that can’t be found in dictionaries (“password”), aren’t common phrases (“HappyDays”), aren’t obviously repetitive (“12345”), and don’t include your personal info that can be found easily (birthdates, kids’ names, your zip code).
We have a few tricks for making strong passwords that won’t drive you nuts; or you can use a random password generator online or download Norton’s free password generator for help. Or of course, use a smart app that generates, saves and encrypts passwords like 1Password. (They’re an affiliate and we love them.)
3. Make sure the device you pick has a password for access too. If the monitor comes with a default password (like 1111) or a blank password, be sure to change it and make it strong during set-up.
4. Don’t forget about guest networks that may come with your Wi-Fi service. Disable them entirely or give them a strong password too. As in, not “guest.” In fact, recently we featured some fun ways to display a guest network password.
5. Be realistic. Remember that the likelihood of someone truly hacking into your baby monitor is slim to none, unless you’re Kourtney Kardashian and the paparazzo will do anything for a photo of your baby. (Cute though your own may be.) Digital transmissions from video monitors should be encrypted to make intercepting data really tough. In fact, we haven’t been able to find one confirmed report of a true baby monitor hacking leading to a burglary or any harm to any children at all, even if the photos of someone watching someone else’s baby seems creepy. And it is.
As I told ABC News a while back, there are plenty of better ways to case your home than through your baby monitor. Just make sure your WiFi password is protected to be safe –whether you’re a video monitor user or not — and you’re using a really respected monitor brand.





Great info. Def makes sense. It is all about secure wi-fi home network. if you take steps to protect your overall home wifi than your baby monitor should be good.
That said, i was still concerned when looking for one for our newborn. Though i verified our connection and the cameras connection both had secure logins and passwords
This is a little on the fluffy side. Anyone who understands application security vulnerabilities would disagree with you. Getting your WAP compromised assumes the predator is still in range. This is as far from the truth as you can imagine. Any internet connected device is subject to scanning and probing. Any device used in your home – wired or wireless – capable of accessing the Internet can be attacked through malicious websites, failure to update software – not just the operating system, but ALL applications installed on the device – email phishing attacks, infected USB drives, peer to peer software downloads, and a host of other vectors. Once you have a compromised device on your internal network – wired or wireless – that device can be used as a jumpbox to laterally spread across your entire home to anything on your network via poor password management or existing vulnerabilities. This includes your IP enabled camera system. Dismissing this as “it only happened to people who did not do the basics” is an ostrich approach. We know how well the ostrich approach has worked at Target, The Home Depot, Staples, Michaels, and many, many, others. Any time you add a device to your network – wired or wireless – you add an administrative chore – maintaining the device, ensuring the latest security updates are applied, and routinely changing the passwords used to access the device. Choosing to ignore this will only result in finding your network pwned by some miscreant. Think before you connect, and decide if security or convenience is more important to you.